Decentralized finance continues to attract new users at a rapid pace. While this ecosystem touts lower fees, open access, and rapid transactions, many of the very same aspects also attract scammers. Criminal groups have significantly moved toward wallet-drainer kits, fake support accounts, and phishing networks built to empty wallets in seconds.
Recent reports show that global crypto scam losses crossed 3.6 billion dollars in 2024, with DeFi wallet attacks making up an increasing share of that number. Security companies tracked a sharp rise in automated phishing pages and approval-draining smart contracts that look convincing even to experienced traders.
People still don’t seem to appreciate how rapidly a DeFi wallet can be hacked. Transfers can’t be reversed, and there’s nobody central to complain to, so the only effective defense is prevention.
Below, we break down how DeFi wallet scams work, the red flags to watch for, and the protection steps that matter. This will go a long way in helping readers stay safe without feeling overwhelmed.
What Is a DeFi Wallet and Why Scammers Target It?
A DeFi wallet is a kind of self-custody utility that enables the storage of crypto, signing of transactions, and interaction with decentralized apps. It holds private keys and seed phrases that are the only proof of ownership. Whoever gets access to those keys takes full control over this wallet. There is no bank, no recovery desk, and no authority that can undo a stolen transaction.
This foundational setup has turned DeFi wallets into one of the main targets for scammers. In fact, the broader decentralized finance ecosystem is frequently targeted by tactics designed to exploit unsuspecting users, from fake tokens to impersonation schemes, which you can explore in more detail in our guide on DeFi scams.
The moment a victim signs a malicious approval or shares the seed phrase, the attacker can drain funds instantly. Anonymity in blockchain networks allows scammers to disappear, while the speed of operations in DeFi helps them move stolen tokens through mixers or cross-chain bridges before the victim has even noticed.
How DeFi Wallet Scams Work and Trap Users?
Most DeFi wallet scams follow a simple pattern. Scammers trick users into signing something they do not fully understand or handing over sensitive information. Once that happens, attackers use automated tools to drain the wallet, swap assets, and move the funds across chains.
These schemes often rely on social engineering, fake websites, impersonated support accounts, and malicious smart contracts that request broad permissions. Many of these attacks are powered by pre-made phishing kits and AI-generated interfaces that look almost identical to real dApps.
The goal is always the same. Create pressure, confusion, or false urgency so the victim clicks or approves something without checking it.
Most Common DeFi Wallet Scams You Should Know About
Scammers continue to evolve their methods. Many now rely on prebuilt toolkits sold on Telegram channels or dark web forums, which makes these attacks faster and more polished. Below are the most prevalent DeFi wallet scams.
Wallet Drainer Scripts
One of the most widespread threats this year is wallet drainer kits. These scripts work by copying the layout of a real DeFi platform and convincingly fool users into signing harmful permissions. Once the approval goes through, the script drains the wallet by swapping the tokens, sending assets to attacker-controlled addresses, and clearing evidence.
Why These Scams Continue to Grow:
- Cheap drainer kits are sold as subscription packages.
- Attackers use AI to clone real interfaces.
- Scripts can bypass simple pop-up warnings.
- Many victims only realize the approval after the funds disappear.
Red flags:
- A page that requires several signatures of approval
- A connection request from a site that looks “almost” right
- Strange token permission prompts
Bogus Wallet Applications
The app stores and unofficial download sites are being inundated with fraudulent mobile wallets and browser extensions. They bear names and logos similar to those of trusted brands. Once installed, they ask for seed phrases during initial setup or silently intercept every action taken inside the app.
How these apps steal funds:
- They transmit seed phrases to remote servers.
- They log every transaction and private key
- They redirect users to phishing dApps.
This trend has grown with the rise of deepfake-style branding, in which scammers are reproducing logos, color palettes, and onboarding flows with high accuracy.
Phishing Sites and Fake Airdrop Claims
Phishing remains one of the biggest entry points for wallet drainers. Fake airdrop pages promise “free tokens” in exchange for connecting a wallet. Once connected, the page pushes malicious approvals or asks users to “verify ownership” by entering seed phrases.
Current trends:
- Links spread via fake X giveaway bots
- Attackers hijack Discord servers to promote scam airdrops
- Scammers clone entire dApps using one-click phishing kits
For readers interested in the social engineering aspect of these types of attacks, see the guide on social engineering scams.
Rug Pulls and Malicious Smart Contracts
Users who jump into new tokens or staking pools without research run the risk of a rug pull. There’s a launch of a token, hype is created, and once enough money enters, the developers pull liquidity or manipulate contract permissions.
Common methods:
- Approval farming
- Hidden mint functions
- Unlimited spending permissions
- Fake liquidity locks
Reports from several security firms indicate an increase in quick-deployed contracts carrying out rug pulls within hours of their launch. The speed makes it hard for users to verify legitimacy before investing.
Bogus Technical Support or Helpdesk Accounts
They pose as support teams for popular wallets and exchanges. They reach out via Telegram, Discord, or X with the offer to “fix issues,” “resolve wallet errors,” or “help recover funds.” Their ultimate objective is usually to obtain seed phrases or gain remote access to a device.
Typical tactics:
- Form support from fake customers asking for recovery phrases
- Screenshare requests
- Urgent warnings claiming the wallet is compromised
No legitimate support team will need a seed phrase. Any request for one should be treated as an immediate red flag.
Investment Schemes and Yield Farming Traps
These scams promise extremely high APY returns through either staking, lending, or liquidity pools. Once the user has deposited their funds, operators manipulate the contract, drain liquidity, or lock withdrawals.
Why these schemes work:
- Victims are convinced that they are dealing with actual DeFi platforms.
- Scammers use trusted influencers or fabricated testimonials.
- Some of these schemes are related to romance scams where fraudsters gradually gain the emotional trust of victims and then influence them into using fake DeFi platforms.
Real-World Case Studies and 2025 Data Snapshot
Over the past couple of years, DeFi wallet scams have been increasingly organized. Security teams are seeing coordinated campaigns where phishing sites, fake support accounts, and wallet drainers all work in concert. Below is a quick snapshot of notable cases representing the current threat landscape.
Recent Cases Highlighting How These Scams Play Out
| Case | Scam Type | Estimated Loss | What Happened |
| User approvals exploited on a cloned staking site | Wallet drainer script | USD 1.2 million | Victims connected wallets to a fake version of a popular staking platform. The page pushed hidden approvals that let attackers drain funds instantly. |
| Fake browser extension listed under a familiar wallet name | Fake wallet app | USD 350,000 | A near-identical extension captured seed phrases during setup. Funds were siphoned within minutes. |
| Airdrop campaign promoted by compromised X accounts | Phishing and fake airdrops | USD 800,000 | Users clicked links to an airdrop that asked for connection permissions. The contract had unlimited token spend rights. |
| New memecoin promoted on Telegram | Rug Pull | USD 2 million | Developers pulled liquidity after a large inflow. Contract analysis later showed hidden functions that allowed minting new tokens at will. |
| Impersonated a support agent on Discord | Fake technical support | USD 90,000 | Scammers convinced a user to “verify” wallet ownership through a seed phrase submission form. |
What These Cases Reveal?
- Most attacks succeed because the victim is trusting in a familiar logo, username, or platform layout.
- Approval-based theft is now more prevalent than the theft of seed phrases because it doesn’t raise suspicion.
- Scammers move funds through cross-chain bridges within minutes; options for recovery are limited.
- Social media has continued to be a major launchpad for these attacks.
These patterns show why users need to review every approval and verify every link, even when a page appears to be completely genuine.
How to Spot a DeFi Wallet Scam Early?
Most scams show signs long before the actual theft happens. The challenge is noticing them in time. Many users trust familiar logos or interfaces, which gives scammers an easy way in. Keeping an eye on a few common warning signals can prevent most attacks.
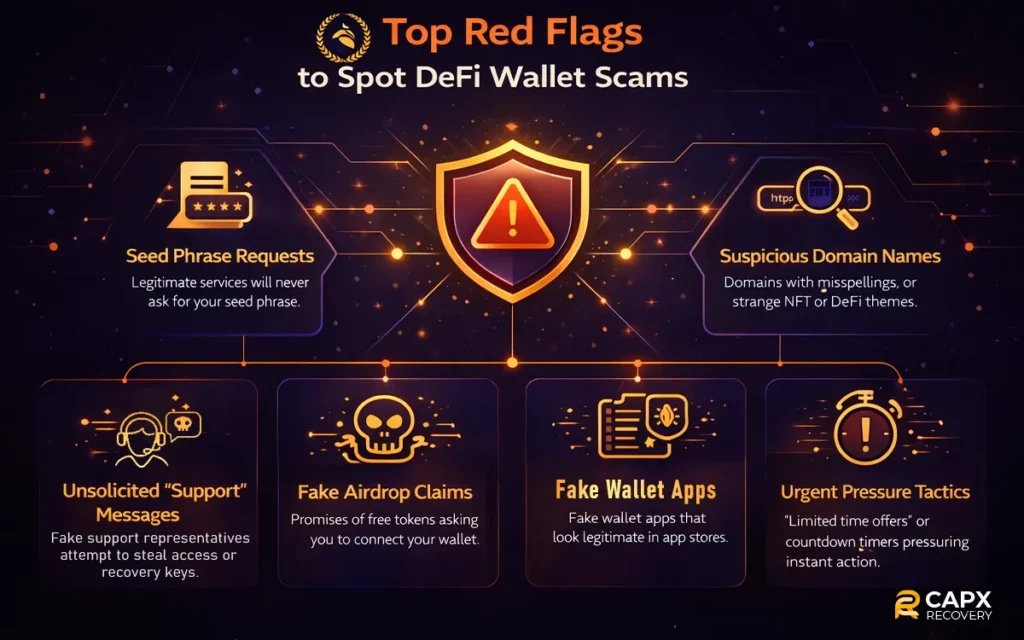
Key Red Flags
- A site or app asks for a seed phrase
- Approval prompts request unlimited token access
- The domain name looks slightly off
- Messages from “support” accounts appear out of nowhere
- Airdrop pages require connecting a wallet to claim rewards
- Apps that look like trusted wallets but come from unofficial stores
- Sudden pressure to act fast or fix a fake “wallet issue”
Quick Red-Flag Reference
| Warning Sign | What It Usually Means |
| Unlimited spend approval | A malicious contract can drain your assets |
| Seed phrase request | Total wallet takeover |
| Link sent through Telegram or Discord | High phishing risk |
| Fake error message on a dApp | Trigger to connect to a fraudulent site |
| Browser extension with a similar name | Possible wallet clone |
When any of these appear, stop and verify the source. Most scams rely on quick reactions, not careful decisions.
How to Protect Your DeFi Wallet From Scammers?
Strong security habits make the most difference in preventing wallet compromises. Scammers depend on rushed decisions, confusion, and weak setup choices. A few simple practices can block most attacks and reduce the chances of losing funds.
Use Hardware Wallets and Multi-Layer Authentication
Hardware wallets remain the safest method to store long-term holdings. They hold private keys apart from online threats and require physical confirmation for each transaction. Most of the recent models already support passphrase layers that create an additional barrier should the device ever fall into the wrong hands.
Helpful habits:
- Use a hardware wallet for anything you cannot afford to lose
- Keep your passphrases offline and stored in two secure locations.
- Enable PIN protection and device lockouts
Smart Contract Permissions Verification
Most wallet drains occur via malicious approvals. Check before signing what permission the contract is requesting. If it says “unlimited spending,” pause and confirm the site is authentic.
Best practices:
- Review approvals on trusted sites
- Revoke old permissions you no longer use
- Double-check domain names before connecting your wallet
Always Download Wallets from Official Sources
One of the fastest-growing scams involves fake apps. Only download wallets or browser extensions from verified sources, like official app stores or the project’s main website.
Things to check:
- Developer name
- Popularity and reviews
- Exact spelling of the wallet name
- Links from the project’s official social channels
Stay Alert for Social Engineering
The majority of the DeFi scams are based on social engineering. Attackers create fake urgency, impersonate support agents, or pretend to be known influencers.
Warning signs:
- Someone contacts you first about a “wallet problem”
- Requests to screenshare or enter a seed phrase
- Suspicious links from Telegram, X, or Discord groups
Verify Real-Time Threat Alerts
Leading wallets and security researchers push real-time alerts on when a domain looks suspicious or a contract has red flags. Staying informed will help you avoid new scam variations.
Most reliable places to check:
- Trust Wallet threat alerts
- Group-IB intelligence updates
- Scam reports from major exchanges and security platforms
What To Do If Your Wallet Is Already Compromised?
Quick action can sometimes save remaining funds.
Steps to take:
- Disconnect the wallet from all dApps
- Revoke all active approvals
- Transfer any remaining assets to a secure hardware wallet
- Review recent activity to identify what was signed
- Avoid interacting with the compromised wallet again
If the loss is significant or involves a coordinated attack, users can explore cryptocurrency scam recovery services for help with tracing and documentation.
When to Seek Professional Help After a DeFi Wallet Scam?
Some situations call for expert support, especially when the scam is complex or the losses are large. Professional investigators and recovery specialists can help trace stolen assets, prepare reports for exchanges, and guide victims through the steps needed to improve the chances of freezing or flagging suspicious wallets.
It makes sense to seek help when:
- Funds move across several chains within minutes
- The scam involves approval drains or malicious contracts
- Fake support agents tricked you into sharing sensitive data
- Multiple victims seem to be involved in the same attack
- Law enforcement or exchanges request detailed evidence
Recovery specialists can also help document every step of the incident, something many victims struggle to do on their own. This documentation becomes important when filing complaints or working with regulated platforms that monitor suspicious transactions.
Get Knowledge and Be Safe
DeFi offers a lot of freedom, but that freedom comes with responsibility. Scammers count on rushed clicks, confusing approvals, and pages that look almost real. The simplest way to stay safe is to slow down, double-check every action, and treat every unexpected message or link with caution. Strong security habits and reliable tools stop most threats before they do any damage.
The space keeps evolving, and new scams appear often, so staying updated is just as important as securing your wallet. With the right mindset, users can enjoy everything DeFi offers while keeping their assets protected.
FAQ
Can stolen crypto from a DeFi wallet be recovered?
Recovery is difficult because transactions are irreversible, but it is not impossible. Quick action, proper documentation, and expert support increase the chances of tracking and freezing funds.
Why do scammers ask for unlimited token approvals?
Unlimited approvals give attackers full spending rights. Once granted, they can drain tokens without needing further permission from the wallet owner.
Are hardware wallets safe from these scams?
Hardware wallets protect private keys, but they cannot stop users from signing harmful approvals. They are safer than software wallets, but still require careful review of every transaction.
What should be done if a suspicious link is clicked?
Disconnect the wallet immediately and avoid signing anything on the page. Check permissions, revoke unknown approvals, and move assets to a secure wallet if needed.